|
The following are answers to commonly asked questions about the first coursework. We will add to this FAQ as new questions come up. Please check here before emailing course staff about coursework confusions.
cd /tmp
du -hS
There are two common causes for this, both of which require you to delete the VM in VirtualBox and then re-import the VM to fix the issue.
The first cause is that you have switched DICE computers. You are installing the VMs into the /tmp directory of the local computer which means that it will not travel with you to a new computer. But the link in the VirtualBox application does travel with you. So VirtualBox is looking for a file that does not exist.
The second cause is because the computer you were on before has been rebooted. When DICE computers are rebooted they automatically delete everything in the /tmp directory. Since that is where your VM was stored it will have been deleted.
For this problem a "security risk" is one row (or top level items in Mallet) in the OpenVAS report. Each row in the report is roughly linked to a single service being provided by the machine. It may be easier to think of the question like this: imagine you only had the budget to address the issues listed in four of the rows. Which rows would you pick and why would you select those ones?
In the following screenshot two potential "security risks" would be "http (80/tcp)" and "ftp (21/tcp)". As can be seen in the screenshot, there are several security holes, warnings, and notes. But what I am looking for is the top level protocol and port along with a description of why you think that one should be prioritized over others. You should be using the security holes, warnings, and notes when formulating your answer.
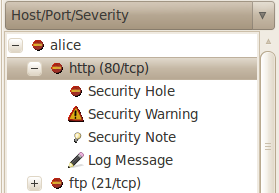
The goal of this exercise is to get you to run OpenVAS and then think about the response at a deeper level than just taking the top four because OpenVAS says so. The answer may very well be to take the top four, but you need to be able to explain why those ones are important and justify your decision.
|
Informatics Forum, 10 Crichton Street, Edinburgh, EH8 9AB, Scotland, UK
Tel: +44 131 651 5661, Fax: +44 131 651 1426, E-mail: school-office@inf.ed.ac.uk Please contact our webadmin with any comments or corrections. Logging and Cookies Unless explicitly stated otherwise, all material is copyright © The University of Edinburgh |